It’s 2021 and We Still Don’t Know How to Give Password Advice
- Founder FridayPasswordsHacking

On a sunny Thursday morning in late 2008, I was sat in a top floor office overlooking Canary Wharf in London's Docklands. How? What was this? Staring at a screen of characters, it looked like noise. Like a 2-year-old had randomly been pressing keys on the keyboard.
I was staring at the log files of a key logger. A particular type of virus that targeted the online bank accounts of the rich and famous. The virus quietly waited, and at the perfect time, it copied down passwords, account details and secret phrases.
I knew what I was doing, but this was not easy. Finding a needle in a field full of haystacks sprang to mind. This was part skill, part art. I understood why hackers offered to extract passwords from this data as a paid service. They were competent, knowledgeable, and likely had a profitable business.
To help solve the problem, I went back to basics and asked – what is a password?
What is a password?
It's a secret that has been shared and proves you know something… that's it.
For 700 years, the night watch of the Tower of London has used 'The Word'. A password that changes every day to grant access after the Ceremony of the Keys. And my children use passwords to grant access into their secret dens, "What's the magic word?".
To use a password, a computer needs to know your secret. So that's why every new computer asks you for it (twice). It then stores your secret in files like /etc/shadow or SAM.
And that is where the problem starts…
As humans, we see a computer as a keyboard and screen for typing words and sharing meaning. But as a security expert, I also see a computer as a set of files and algorithms. Find the correct file, try all the combinations, and I get your password. I cracked it.
In 2021 we have arrived at a strange place. As xkcd cartoonist Randall Munroe put it, "Through 20 years of effort, we have correctly trained everyone to use passwords that are hard for humans to remember, but easy for computers to guess." And Bill Burr, the man behind the vast majority of the trusted tips and tricks we have traditionally used to create passwords, regrets his advice. Saying in an interview with the Wall Street Journal, "Much of what I did I now regret".
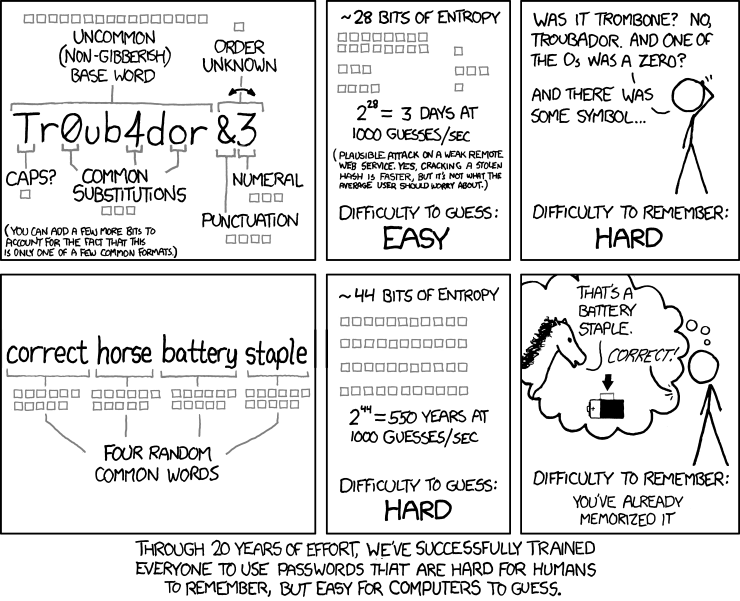
Password Advice in 2021
If you look for password advice in 2021, you will get 2 very different sets of guidance. One taking a traditional security experts view, and the other taking a human perspective. Seemingly the only thing both groups of advice can agree on is – to only use passwords once. That is, don't use the same password across all your social media accounts.
The Traditional Security Experts View of Passwords
Typing 'how to create a strong password' into Google, you will receive much of the traditional security expert advice:
- Make it long – at least 15 characters
- Don't use common dictionary words
- Use a mix of characters - mix up letters (upper-case and lower-case), numbers, and symbols
- Change your passwords regularly
This is the view that Randall Munroe and Bill Burr are concerned with. The loose idea being, if a password is made up of $#@! mixed with a few numbers and some grammatically incorrect letters and changed frequently enough, all will be well. It has been the advice the US National Institute of Standards and Technology (NIST) has promoted for many years.
While this approach may be more secure from a mathematical perspective, it creates hard to remember passwords and leads people into using just one password.
The Human View of Passwords
The human view of passwords, in contrast, has been championed by the National Cyber Security Centre in the UK for the last five years. It uses a simple phrase as guidance: three random words or #think random.
In an August 2021 post, the author of this guidance explained the thinking behind it. In essence, make passwords more usable and easy for people to use different passwords on their accounts.
The Future of Passwords
While there are regular calls that passwords are obsolete – "use passwordless", "use 2-factor" – there remain many situations and services where passwords are the only option.
So which is the correct guidance?
It is important to note that NIST has softened their security expert view of passwords in their most recent advice. They are less concerned with random ^$*% and more concerned with the length of the password. Similarly, there is no need to change the password regularly.
Personally – I care about humans and the usability of security, so I recommend the NCSC approach. If you are concerned about passwords being too short – try 4 or 5 words instead of three. After all, a study from the 1950s says most people can remember between 5 and 9 words, and who am I to question 65-year-old research. 😀