Fresh Thoughts #89: Market Dynamics and Malware Detection
- Newsletter

Market Dynamics and Malware Detection
If you saw me flash a wry smile at a recent Heimdal presentation - just when the CEO said:
"We don't do XDR anymore. We do MXDR."
It wasn't the jargon-laced sentences.
It was the entirely predictable market dynamics forcing his business to change.
All business practices, knowledge and activities evolve.
Starting as novel, uncertain and scarce.
And ultimately becoming common, certain, and a utility.
Knowing where a technology is in its evolution helps predict what will happen next (although not when).
And helps answer the all-to-common question...
Does this newly hyped thing or sales narrative make sense?
I've been using this idea of evolution for over a decade since I learnt about Wardley Maps; a way of looking at a business landscape and understanding how different strategies will help or hinder competition.
As an activity - like detecting malware - becomes more certain and more common, it goes through four evolutionary phases:
- Genesis: When nothing is certain, and the opportunities appear wondrous... if only you can do it.
- Custom built: When questions become "How do we...?" and the focus is on building.
- Product (+rental): When the market demand rapidly increases, and the focus is on operations and maintenance at scale.
- Commodity (+utility): When the activity is well understood, everyone who wants one has one, and conversations are about how to use the thing efficiently and effectively.
Evolution Takes Time
It took 65 years for electronic computers to pass through all four stages - from the first Z3 computer in 1941 (Genesis) to the announcement of Amazon EC2 utility computing in 2006 (utility).
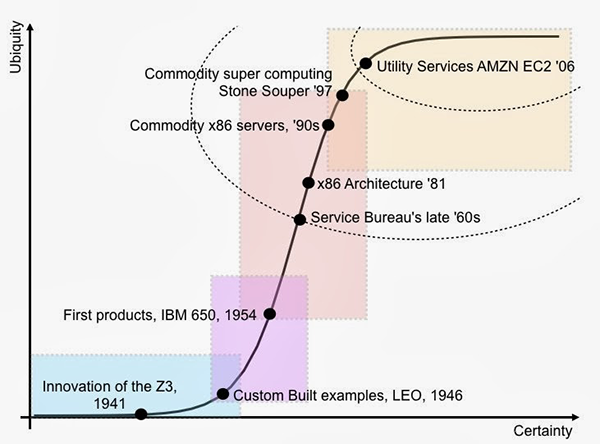
From: https://blog.gardeviance.org/2010/11/all-in-word.html.
But the most disruptive innovations don't happen within an evolutionary phase. They happen when activities cross a boundary into a new evolutionary stage.
I occasionally hear that cloud computing is "just someone else's computer". But in reality, it is the evolution of computing from being a product to becoming a utility.
I lived through this transition.
My experience buying, racking and networking Dell "pizza boxes" servers in 2005 differs wildly from "creating an instance on AWS EC2" in 2023.
No industry is immune from evolution.
That includes detecting malware.
The Evolution of Malware Detection
Malware detection became a utility on 26 October 2012.
That day, Microsoft released Windows 8 with Windows Defender included in the operating system as standard, at no additional cost.
The inevitable consequence of this strategy took 10 years to appear. When - in 2022 - IDC ranked Microsoft Defender as the number one in market share in the Corporate Endpoint Security market.
This consequence was inevitable because Microsoft used an economic driver called Jevon's Paradox: as technological progress or policy increases the efficiency of using a resource, the demand for that resource will increase.
Microsoft made Windows Defender easy to use in four ways:
- Microsoft had access to the entire Windows market.
- It was installed by default from Windows 8 onwards.
- The base version of Defender had no additional costs.
- Microsoft has managed to avoid monopolistic concerns.
In 2020, IDC ranked Microsoft Defender fifth in the market, albeit with 94% year-on-year growth. By 2022, when other vendors' growth had slowed, Microsoft Defender's growth accelerated to 109% year-on-year.
Last year, Microsoft Defender was:
- Ranked first in terms of market share.
- Growing over 3 times faster than the market.
- Growing twice as fast as its largest competitor.
This is the power of moving malware detection from a product to a utility.
Market Dynamics
I have previously written about the evolution of antivirus to EDR and XDR. While researching that piece, Google Trends produced an interesting graph - which perfectly encapsulates competitor's response to Microsoft's strategy.
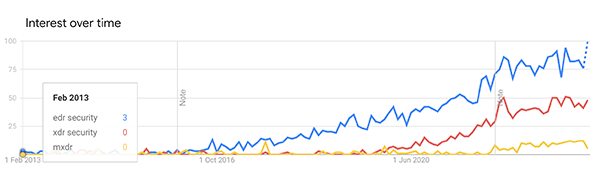
For three years, nothing happened.
Then, in 2016, EDR became an industry search term.
Followed in early 2020 by XDR and MXDR in January 2022.
When markets change substantially, Sales and Marketing departments are tasked with changing the topic and asking customers to focus elsewhere.
The heavy promotion of EDR... then XDR... and now MXDR are attempts to distance from the uncomfortable truth that malware detection is a commoditised utility.
I hear and understand the counter-arguments that XDR, EDR, and simple malware detection are different. However, Microsoft Defender for Endpoint's P1 and P2 plans look an awful lot like EDR and XDR - with a simple upsell to existing customers.
They, too, have become a commoditised utility.
Which meant Heimdall's need to move beyond XDR was inevitable.
And the CEO's comments were just confirmation.


