Fresh Thoughts #25: The Revolutionary Advance of Three Random Words
- Newsletter

Passwords have always been a problem. And it seems password advice has taken every wrong turn possible, creating a terrible experience.
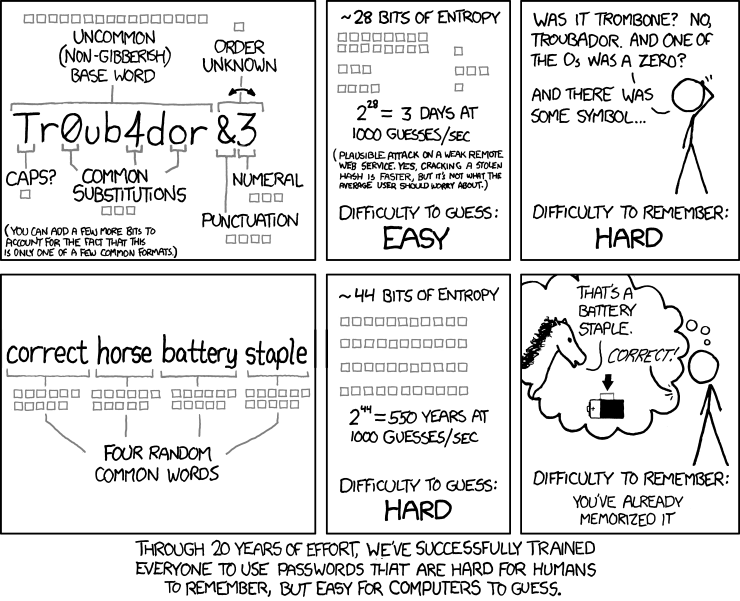
https://imgs.xkcd.com/comics/password_strength.png
Why is 3-Random Words Revolutionary?
In 2016 the NCSC published an idea - create a password using 3 random words.
The NCSC rejected the legacy password rules and started by first thinking about people and experience. It argued against the old advice of:
- Use letters (lower & upper-case), numbers, special/punctuation characters
- Don't use dictionary words
- Make the password as random as possible. 5V$eK2N& is a 'good' password
A Different Way of Looking at Passwords
In short - it's not about the password.
And as the NCSC said at the launch, it's not all maths.
It's about a broader set of advice that works under the banner of 3-random words. It includes focussing on common and likely attacks, creating memorable passwords, and seeing passwords in a broader context.
Focus on Common Attacks
The traditional way of looking at password security is based on:
"If I had unlimited guesses and a vast number of computers... I could try every combination of characters and guess your password."
This is called a Rainbow Table or brute force attack.
Fortunately, this situation is rare. The more common attacks against passwords focus on reusing or guessing weak passwords.
People commonly reuse passwords between systems. So if a password is lost or stolen from one site, it can be tried on every other business and e-commerce service.
Similarly, the most common passwords are well-known. Unfortunately, people habitually think alike and use "123456". So if an attacker has a list of email addresses, it's easy to try the 100 most common passwords for each account.
This is called a password spray attack.
And so, the NCSC guidance focuses on these attacks and comes with additional advice:
- lock accounts after 10 unsuccessful password attempts
- promptly change known or suspected compromised passwords
- use a deny list to block common passwords
Memorable Passwords
Cybersecurity and terrible experiences are nothing new. Back in 2009, Microsoft Research published a paper on the rational rejection of security advice by users.
So making memorable passwords is at the heart of the NCSC guidance. What could be easier than 3 random words?
The Rule-of-3 feels natural, normal. It's been around since Aristotle wrote Rhetoric and can be found in everything from jokes to web apps... What3Words?
To be more accurate, the NCSC advice should read "at least 3 random words". But it has less marketing appeal...
As the NCSC no longer requires special characters and numbers, the password must be longer. One way to think about this approach is - the password must be long enough to foil common attacks.
While the legacy advice requires passwords to have 8 characters, using just three 4-letter words makes the password 50% longer.
No regular password changes
A quieter but equally revolutionary part of the guidance is that everyone should stop changing their password every 3-6 months. This has long been - just the way things are done. But the NCSC clearly says - No!
Research has found requiring regular changes leads people to choose simpler passwords rather than being a security benefit.
To be clear, the advice is not never to change your password. Instead, only change it when you suspect or know it has been lost or stolen.
It's Got to be Random
But all of the 3-random word guidance isn't new. The NCSC walks a fine line when it comes to random words.
While using dictionary words is okay, they have to be random. It's no good if you have three children - whose names are all over social media - and they're also your 3-random words.
Your password will be known in one guess.
Ensuring that words aren't easily discoverable is one of the trickier parts of implementing this guidance and relies heavily on security awareness training.
In some cases, I've heard "pack.golf.curl" is becoming the new "123456".
Passwords in context
Finally, this advice should be seen in the broader context of the NCSC strongly pushing multi-factor authentication (MFA).
We've previously commented on the NCSC requirement that all cloud services must use MFA. And while remaining an aspiration, it is a critical audit point on NCSC's Cyber Essentials certification.
If a cloud service doesn't support MFA - you can still pass Cyber Essentials, but you must list exactly which cloud services are in violation.
Final Thoughts
The 3-random word revolution is far from over. The traditional approach of random characters and numbers is still the advice from some security frameworks - like CIS Controls v8.
However, some of the less radical parts of the guidance have been adopted. For example, the NIST Special Publication 800-63B advises against regular password changes. But there hasn't been the full adoption of 3-random words.
I speculate this is because of the sheer number of systems that would need to be modified to make such a revolutionary change.


