Fresh Thoughts #92: The Legacy Game: How Tech Vendors Are Missing the Mark
- Newsletter

Last week, I wrote about how the decision to buy virtual reality headsets, AI-driven marketing and laptops for staff follow different patterns.
VR headsets for the classroom or office are bought because you love the idea. However, buying a laptop or phone is rarely a passionate purchase.
It made me wonder - from the other side of the fence... do vendors know what game they are really playing?
From my mid-career, watching the emergence of cloud computing, I saw many vendors playing a legacy game of selling and marketing products and services. All while, Amazon Web Services emerged as a commodity/utility provider solving the exact business needs - and became the $20B+ per annum business it is today.
I am increasingly getting a sense of deja vu.
As recent marketing examples tell me, many long-time cybersecurity vendors haven't spotted the winds of change.
Before diving into email security gateways as a recent example, it is necessary to explain the broader picture of evolution in business.
Evolution... Not Just Activities
In my previous newsletters, I looked at the evolution of cybersecurity activities from genesis to commodity/utility. But the idea of evolution applies to data, practices, and knowledge. Moreover - for each phase of evolution - there are common characteristics and general properties in all these areas.
Simon Wardley - the creator of Wardley Maps and the first to outline the idea of evolution in business - created a handy table to see all of these characteristics and properties in one place.
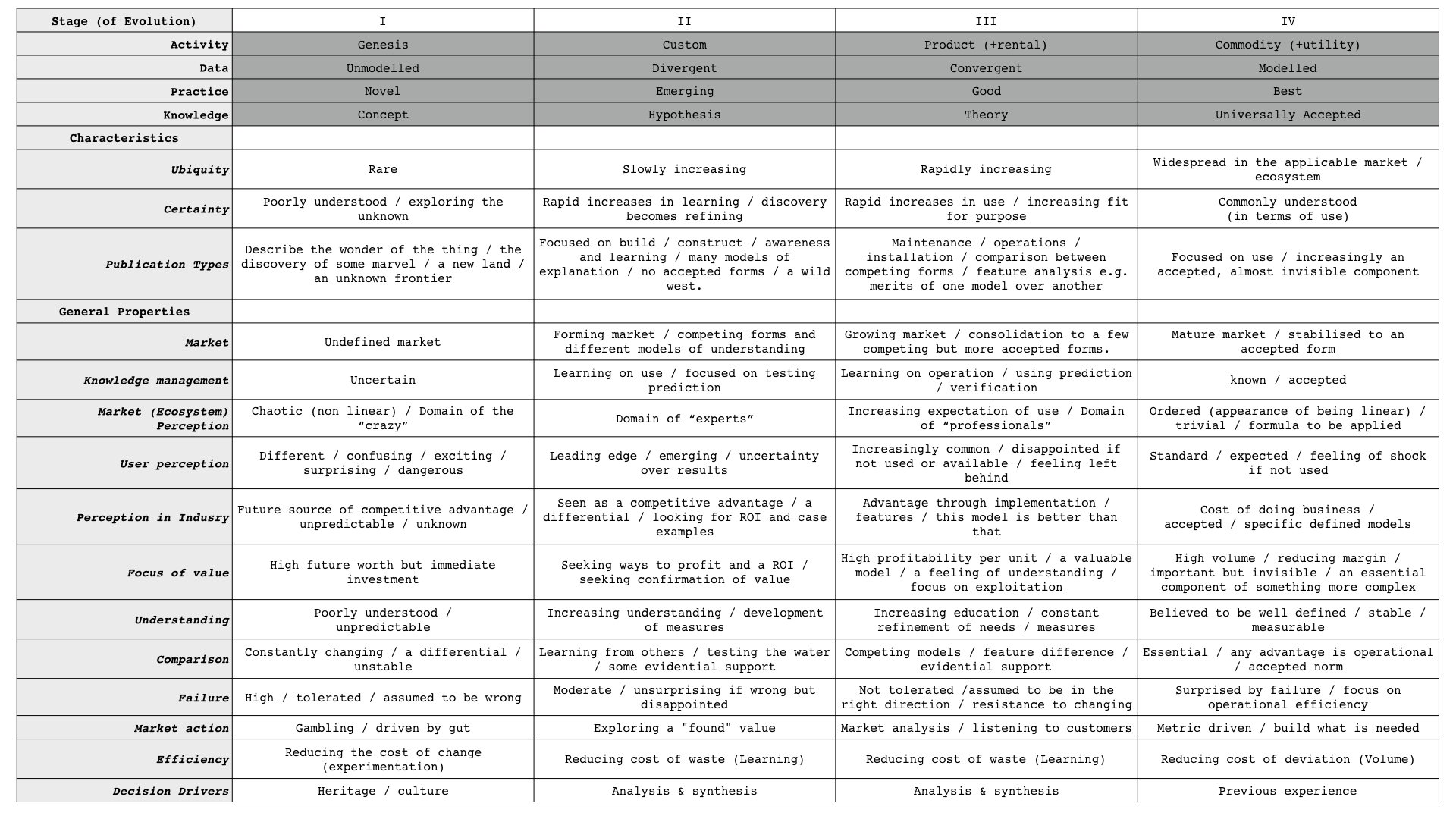
This analysis applies well to any cybersecurity concept. However, a recent presentation by Hornet Security makes email security a valuable and current case study.
The Evolution of Email Security
As the largest email service providers, Microsoft 365 and Google Workspace built-in security act as the industry benchmarks.
In Microsoft's case - their email security offers are Exchange Online Protection and Microsoft Defender for Office 365.
From a market view - Microsoft's focus on "secure by default" and choosing from three standardised security levels - Default, Standard, and Strict - is significant. This leads to a consensus that the Exchange Online Protection configuration is primarily a "set and forget", which is "important but invisible".
From an operator's view, IT administrators are well versed in releasing emails from quarantine, which junior staff can complete by following standard operating procedures.
From a sales view - Exchange Online Protection is available in most Microsoft subscriptions. However, additional features - such as impersonation detection and tuning the sensitivity of machine learning models - come with an extra monthly charge.
These features are worthwhile for senior staff and highly visible people in your business. But may not be widely deployed based on your IT cost sensitivity.
Google Workspace has a very similar analysis.
From the table, email security should be placed in the commodity/utility phase of evolution.
Now, let's consider the other email security gateway vendors.
Legacy Vendors
Recently, I attended a sales presentation from Hornet Security. For almost 20 years, Hornet has sold email security gateways.
As an established vendor directly competing with Mimecast and Baracuda, I was eager to learn how they would differentiate themselves in the marketplace.
After listening for 30 minutes, I was underwhelmed. The entire presentation could be summarised in two points:
- "Choose Hornet because we detect 99.9% of phishing emails compared to Microsoft - who only detect 99%."
This left me asking - Is a substantial monthly subscription payment worth the extra 0.9% improvement?
For some, certainly... but for most... 🤔. - "We are expanding and becoming a security platform..." - which boiled down to offering backup services, security awareness training, and other industry-standard features consolidated onto a single platform.
If this reminds you of Heimdall's CEO being forced to move into MXDR, I had the same sentiment.
But importantly, these points and the presentation as a whole focused on:
- The advantage of new features
- The superiority of Hornet's security model
- Justifying why it was necessary to pay more for these features
The table suggests this places Hornet in the product/rental space.
"Off With Their Heads..."
In evolutionary terms, Hornet is behind Microsoft 365 and Google Workspace, which is a problem. As evolutionary biology's Red Queen hypothesis tells us, "species must constantly adapt, evolve and grow to survive".
This is a lesson many vendors learnt the hard way during the rise of AWS and the emergence of cloud computing. Resulting in a flurry of revenue-based acquisitions and market consolidation.


